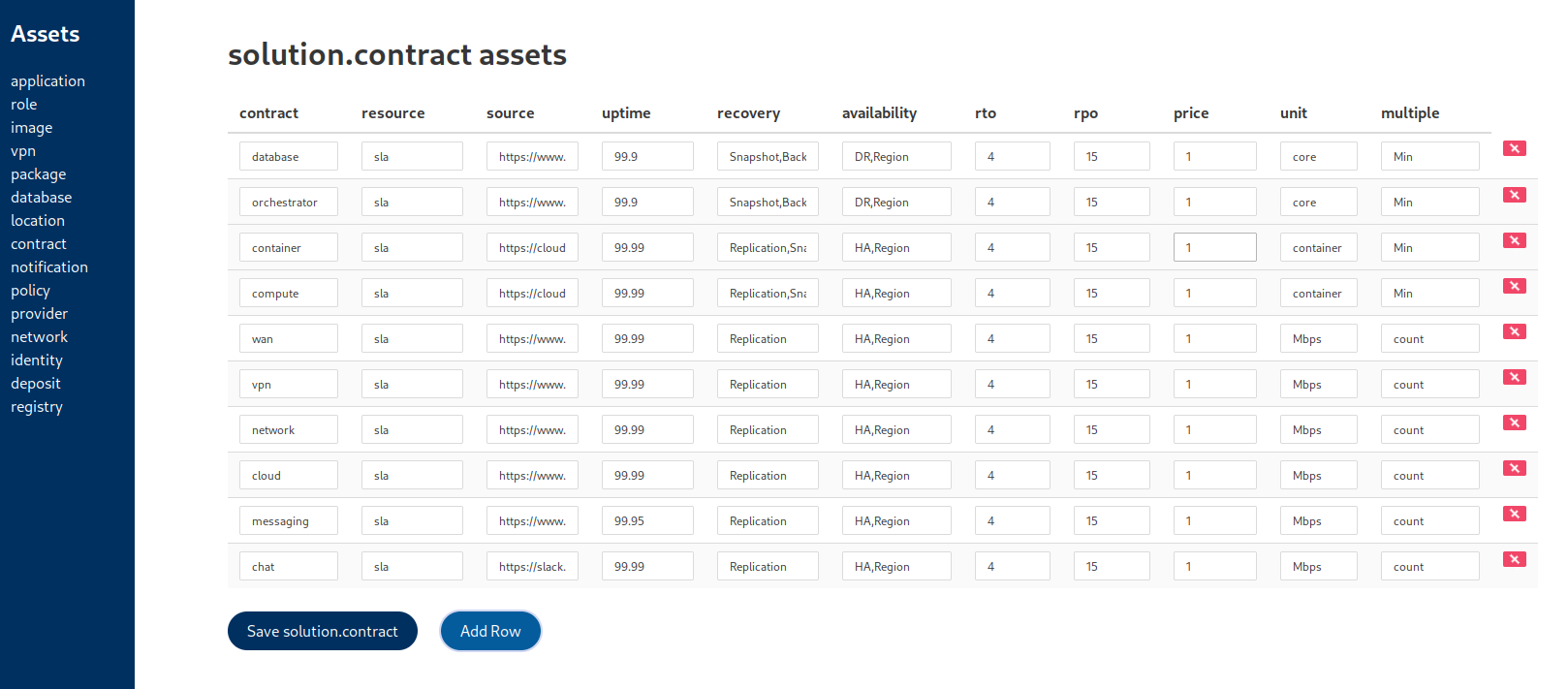
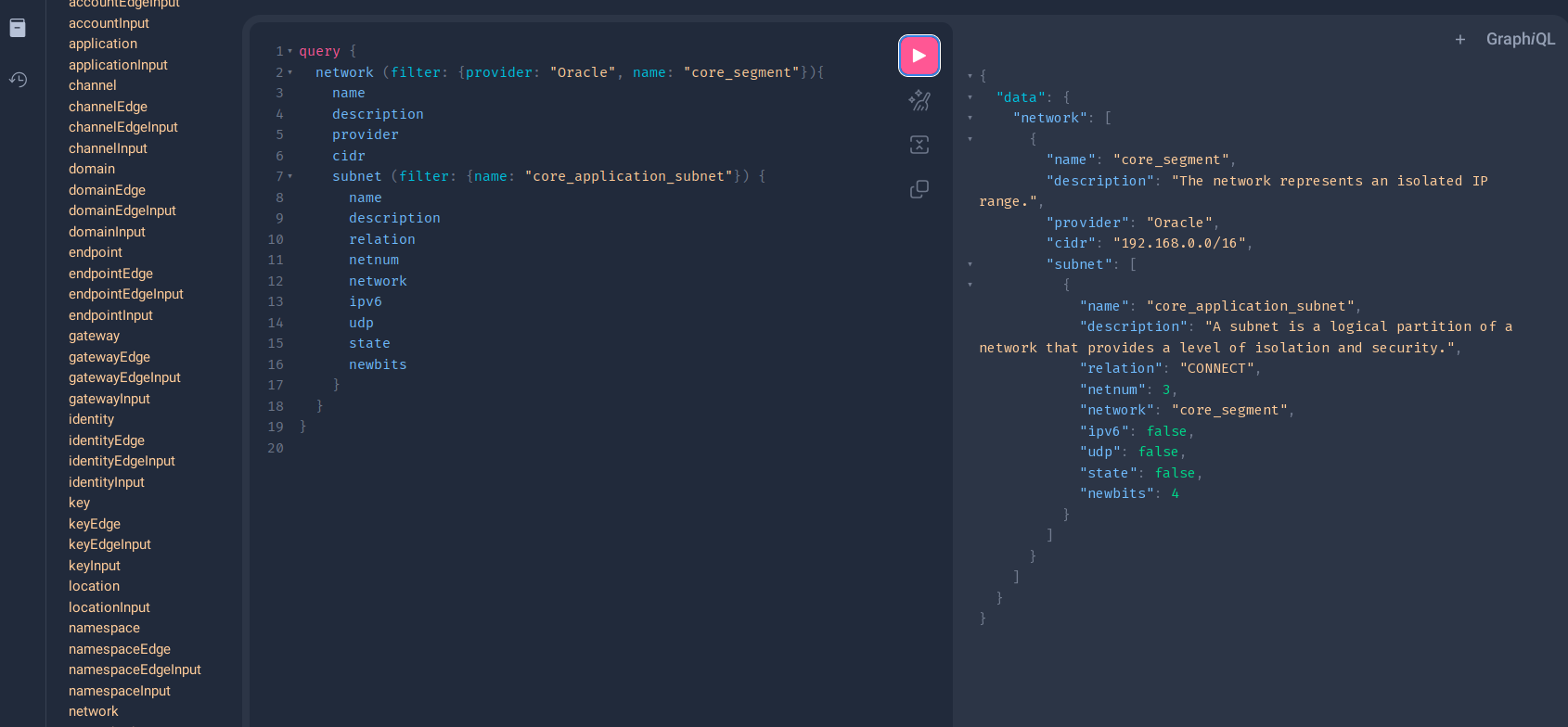
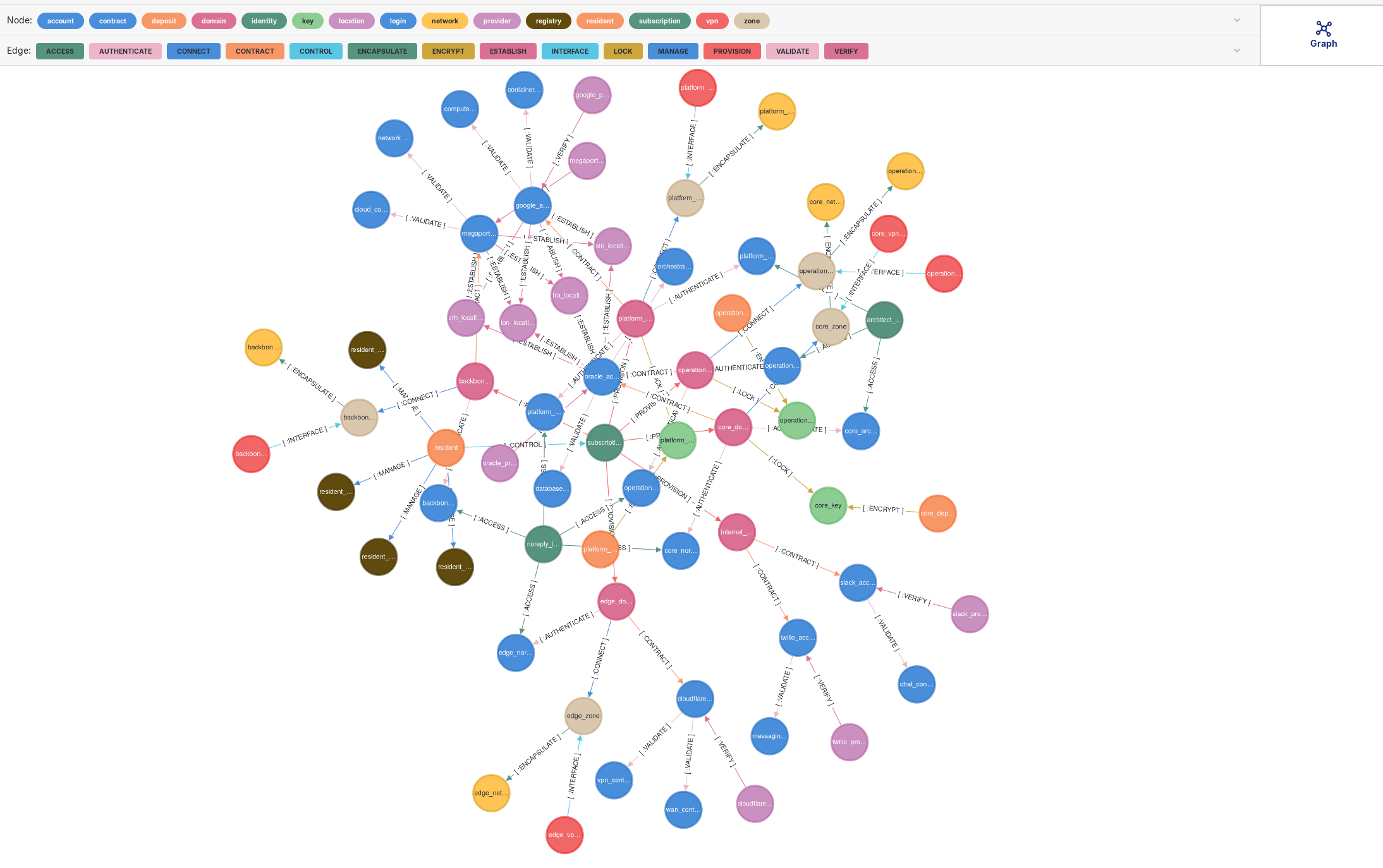
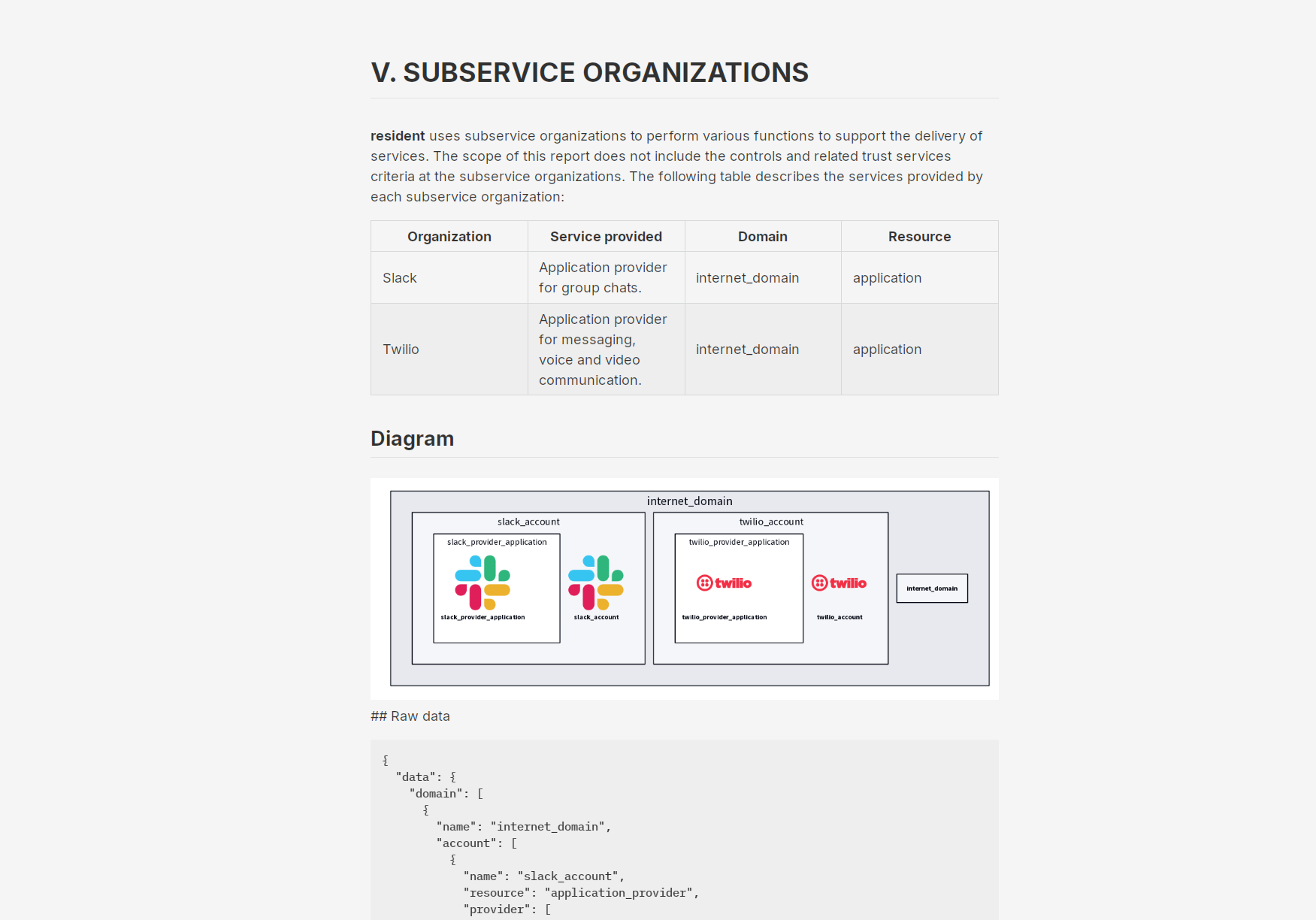
Automate Your Hybrid Data Center
Model your private and public infrastructure as code to streamline service delivery and ensure end-to-end compliance.
Evolve your data center from a cost center to a strategic, programmable platform. By modeling the dependencies between on-premise hardware, virtualized environments, and public cloud services, you create a queryable "digital twin" of your entire estate. This application-centric view unlocks powerful automation, simplifies hybrid cloud management, and makes compliance with standards like DORA fully auditable.